YubiKey 5 for Linux Review
Introduction
Here is where I review how using a YubiKey 5 NFC with Linux worked for me.
Initial Setup
I used the Yubico-Pam setup page for most of this. However, this instruction set seems to indicate that one must build all the components from git or source. I didn't need to do this, as OpenSUSE LEAP 15.4 contains the needed packages.
Note, however, that this instruction set
tells you to first add an auth line that ends in "debug" to
/etc/pam.d/common-auth (it doesn't tell you where to add it, but
that's where all the other lines that start with "auth" are
located. Then the one that specifies the authfile
target. I noticed that LightDM would make me press the
button on the YubiKey 5 NFC more than once. Commenting out
the line that ends in "debug" worked. I also created the
~/.yubico/authorized_yubikeys file like it instructs.
I also didn't need to move any files around, as they already existed in /lib64/security.
I followed the steps for the mappings in /etc/yubikey_mappings and linked both my YubiKey 5 NFCs to both me and my wife's accounts on my Linux machine.
To get the token IDs, I took the last 32 characters from the results of pasting: I opened a MousePad and pressed the button for an OTP.
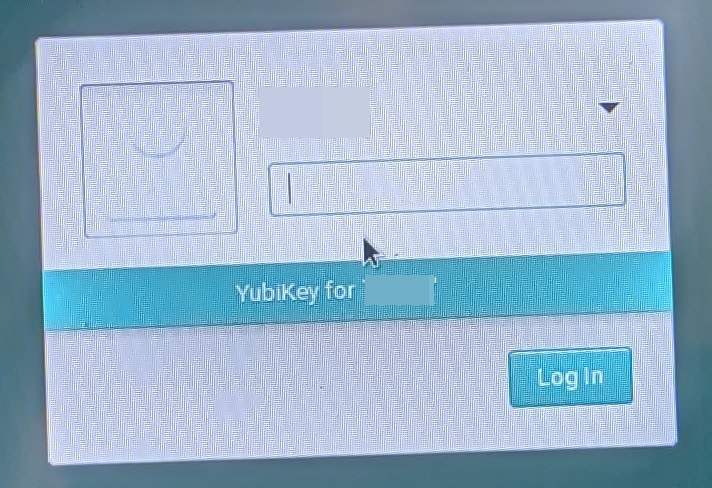
As a result, logging in to LightDM
worked! My apologies for having to take a photo of the
screen to do this.
However, going into the YubiKey Manager, when I click "FIDO2" it gives an error about "7 is not a valid key." I wonder if this means that I won't be able to use it to authenticate.
The YubiKey Authenticator for Linux synchronizes between the mobile and Windows versions, so that should work.
However, I could not find anywhere in Linux PAM documentation where logs are stored. I noticed that some end up in /var/log/warn and /var/log/messages however.
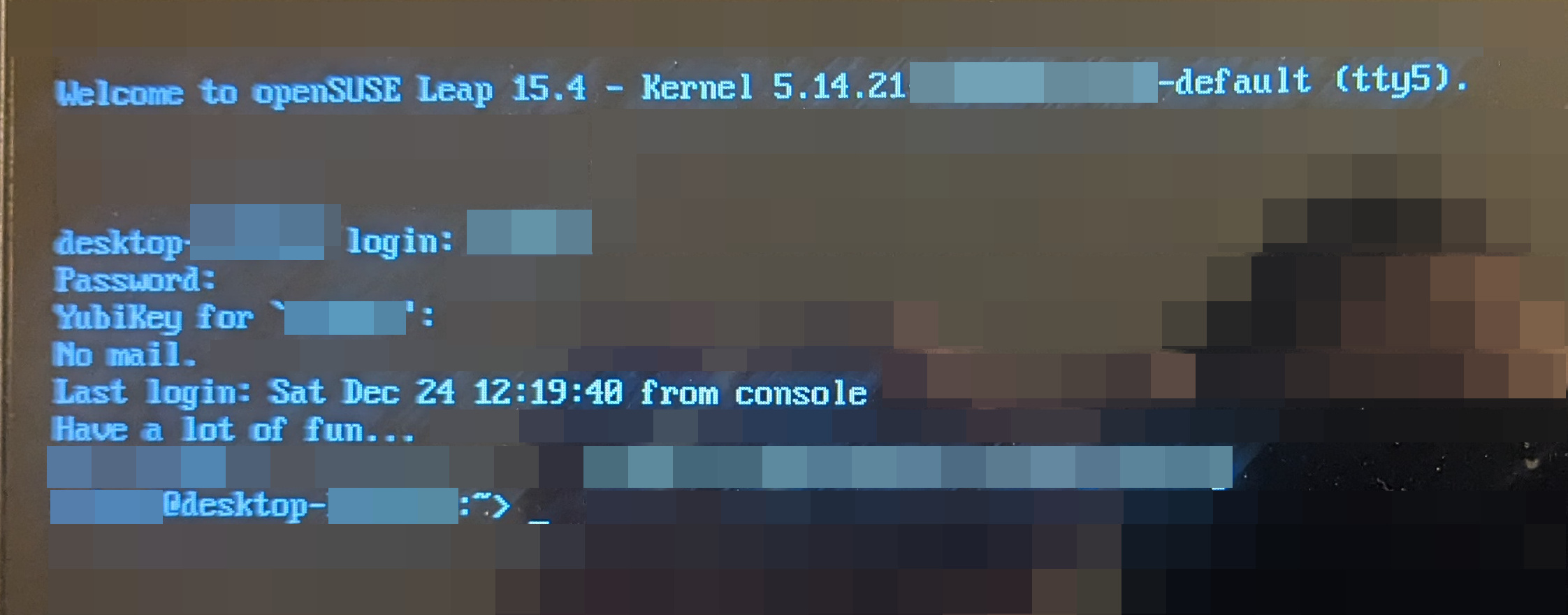
Virtual Terminals are Also Protected
To my surprise and delight, virtual terminal
logins are also protected by YubiKey-PAM integration. Note
that there should always be, in theory, one user account (like
root) which has only password login. So make a very strong
password and use it on this account. This is so you do not
potentially get completely locked out. Alternately, if you
backup your stuff every day, you can mitigate this to a
point. Again, sorry for the external screenshot device.
Dropbox via Chrome in Linux
I could not log in using my USB key in Linux. And for some reason it did not show my Authenticator app as a sign-in option. I even logged in using Linux finally after a lot of pain in the rear to even get in (I had to log in using my mobile app then do the connect QR code thing and then manually surf back to www.dropbox.com), then added a new entry for the Linux version of authentication and it still would not accept my YubiKey 5 NFC via USB. In fact the YubiKey Manager, when I click Applications > FIDO2, says "Error: 7 is not a valid key." I can go to the PIV and OTP pages but not the FIDO2 page. But then why isn't DropBox log in from Linux via Chrome showing my Authenticator app?
So basically I had to make the Yubikey Authenticator the primary mode for Dropbox. It also would not let me register my backup key, key 2. However, what I was able to do is to go back through Authenticator setup.
Re-accomplishing Authenticator Setup
I realized that I had not set my backup key, key 2, to be in the Authenticator. So what I did was go back through all my accounts and delete, then set up the Authenticator all over again. But this time, I saved the secrets the websites generated in a text file saved to my SD Card in my laptop and then record them all for all accounts. So I would set up one account all over again (after making sure I didn't need the Authenticator to get back in, deleting it) and then set it up with key 1. Then I would save the secret to the text file, plug in key 2, add it to key 2, and then both keys had the same Authenticator settings essentially. Then of course, reboot from Windows into Linux, save the file in an encrypted manner and shred the file on the SD card so it can't be recovered.
So basically the YubiKey Authenticator became the primary mode for all applications. This is good only because this Authenticator requires the physical YubiKey. I added the keys themselves physically via USB to all accounts that use them (for instance, Microsoft), but kept the Authenticator as primary so that it would work in Linux and in Windows.


